What is Secure Access Service Edge (SASE)?

Traditional security models weren’t built for today’s distributed workplaces. They rely on fixed boundaries and on-premises hardware, which can make it difficult to protect remote users, enforce consistent policies, or monitor new threats quickly.
Secure Access Service Edge (SASE) offers a modern approach by combining networking and security in one cloud-based system. It helps organizations protect data, control access, and maintain consistent performance across all locations.
In this guide, we’ll break down how SASE works and why it’s becoming the foundation for secure, scalable access in the workplace.
Please note: This article focuses on enterprise networking solutions that organizations use to manage access and secure internal systems. Consumer virtual private network (VPN) apps, such as ExpressVPN, serve a different purpose: they secure personal devices, encrypt everyday internet traffic, and protect user privacy online.
How SASE works
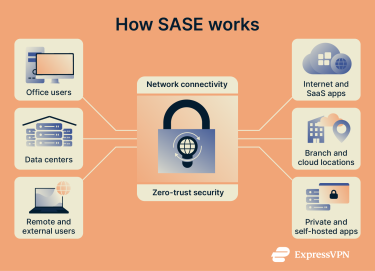 Traditional networks route traffic through a company’s data center before it reaches the internet. This worked when apps and users were in one place, but today, sending every connection through a single hub creates bottlenecks and weak points.
Traditional networks route traffic through a company’s data center before it reaches the internet. This worked when apps and users were in one place, but today, sending every connection through a single hub creates bottlenecks and weak points.
SASE moves networking and security to the cloud, where traffic is inspected, encrypted, and routed directly to the right app or service. This provides faster, more reliable access while applying the same level of protection as a corporate firewall.
With networking and security integrated in the same cloud framework, the same policies apply everywhere, keeping data private and giving teams full visibility into network activity.
What’s inside an SASE solution?
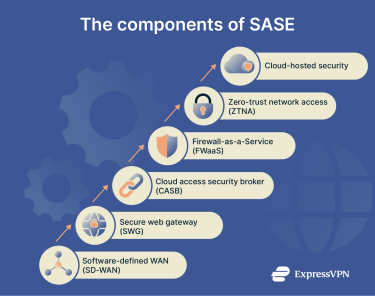 A complete SASE solution combines multiple cloud-based tools to keep your network fast, secure, and easy to manage. Each tool has a specific role, but together they work as a single system to protect every connection.
A complete SASE solution combines multiple cloud-based tools to keep your network fast, secure, and easy to manage. Each tool has a specific role, but together they work as a single system to protect every connection.
Smart routing with cloud-based software-defined wide area network (SD-WAN)
A SASE framework starts with SD-WAN, which keeps your traffic moving efficiently across the internet. Instead of relying on fixed routes, SD-WAN analyzes conditions in real time and sends data along the fastest, most reliable path. It can prioritize business-critical apps, balance loads across connections, and automatically reroute traffic if a link slows down.
SD-WAN is cloud-based, so you don’t need to manage separate routers or private circuits at each location. It connects each site or person to the nearest gateway, where routing decisions happen in real time to keep data moving efficiently. This gives you faster, more stable, and secure connections even if you’re working remotely.
Zero trust: Only the right people get in
Every SASE framework follows a zero-trust approach. Instead of assuming anyone inside the network can be trusted, zero-trust network access (ZTNA) checks every connection before granting entry. It verifies your identity, evaluates device health, and confirms permissions each time you log in, so only approved people and devices can reach company systems.
This approach replaces the old idea of “trusted inside, untrusted outside.” Even if you’re already on the network, you still need to prove who you are and that your device is secure.
In short, zero-trust access depends on verification, not where you connect from, which means you get the same level of protection on public Wi-Fi as you do in the office.
Web filtering that keeps threats out
SASE includes secure web gateway (SWG) technology to block malicious or inappropriate content before it reaches your network. Each time you visit a website or open a link, the gateway checks the destination against threat databases and policy rules. It can help stop phishing pages, command-and-control links, and sites known to host malware, reducing the chance of infection or data loss.
Web filtering works continuously in the background, applying the same protection wherever you go. It automatically enforces safe browsing rules and blocks sites that could expose sensitive data or create entry points for cybercriminals. This helps minimize the risk of breaches and helps improve network resilience against threats.
Protecting your cloud apps automatically
A cloud access security broker (CASB) strengthens the link between your network and the cloud apps you rely on. It monitors traffic in real time, enforcing security policies that stop risky actions before they cause damage.
If something looks unusual, CASB flags it. This might include strange logins, large file transfers, or attempts to access data from unknown devices. It can also encrypt sensitive files and apply data loss prevention (DLP) rules automatically. That way, you can spot unsanctioned apps, control how information is shared, and block suspicious activity as it happens.
Built-in firewall: No hardware needed
Firewall-as-a-Service (FWaaS) moves the role of a traditional firewall into the cloud. Instead of running separate hardware at each office, all your traffic passes through a centralized inspection layer that applies the same security standards everywhere.
The firewall checks connections at the application level, identifying threats that older, port-based systems might overlook, such as hidden malware or attempts to steal data through cloud apps.
It also filters traffic using device and identity-based access rules, so you can allow certain people access to specific files while preventing others from seeing them. These rules extend to online content and services, too. FWaaS can block high-risk or malicious sites before anyone connects to them, such as known domains linked to phishing.
One dashboard to control it all
Managing security becomes much simpler when everything runs through one platform. A SASE framework gives you a single dashboard where you can see your entire network in real time. You can check who’s connected, review traffic patterns, and apply security rules from the same place.
This centralized dashboard also gives you the ability to act faster, while keeping protection consistent. When a new office comes online or a team member joins, you can update access policies immediately. If a threat appears, you can isolate it before it causes damage elsewhere, and roll out a fix across the network in minutes.
Why people choose SASE

Stronger online security, anywhere
SASE strengthens protection through an edge security model that inspects traffic at the cloud edge, which is the distributed network of servers that sits between you and the internet. Each gateway scans your connection before it reaches apps or devices, running it through multiple security checks.
The same security rules apply no matter where you connect from. Firewall protection, threat detection, DLP, and encryption all run automatically at the nearest cloud gateway.
This setup reduces the gaps that can appear when data travels outside company controls, such as when employees use cloud apps over networks the organization doesn’t manage.
Simple for remote teams
SASE makes remote work easier to manage and more secure. In traditional setups, traffic often has to travel through a central gateway or office firewall before reaching the internet.
With SASE, the nearest cloud gateway automatically verifies your identity and device before you can reach company apps or data.
SASE is beneficial for IT teams, too. Teams can manage access policies, authentication rules, and threat protections from one dashboard, and updates reach every person automatically. This keeps remote and hybrid teams protected without relying on multiple separate tools or complicated configurations.
Faster, smoother internet
SASE improves network performance by using SD-WAN to choose the best path for your traffic. It regularly measures connection quality, assessing factors like latency, jitter, and packet loss, then directs traffic through the fastest path. With legacy systems, traffic usually travels through a fixed route or a central hub, which can cause things to slow down.
Security runs in the same cloud framework, so traffic also doesn’t need to detour through on-premises appliances for inspection. Data moves securely through the nearest SASE gateway, where encryption and threat filtering happen at the same time as routing. This helps to establish faster, more stable connections without compromising security.
Grows with your needs
SASE expands naturally as your organization changes. When you add new users, devices, or branch offices, the system applies the same access controls and security policies automatically. You don’t need to install hardware or reconfigure local firewalls, as everything updates through the cloud.
As your traffic increases, SASE adds capacity through nearby cloud gateways that share the workload and keep connections steady. The network scales almost instantly, so performance and protection stay consistent no matter how quickly you expand.
SASE vs. other options
SASE brings networking and security together in one cloud-based model, but it’s not the only way to protect and manage your network. Let’s explore how SASE compares to other options.
SASE vs. business VPN: What’s the difference?
| Business VPN | SASE | |
| Connection | Creates an encrypted tunnel between your device and the company network | Connects you to the nearest secure cloud gateway that verifies and filters traffic |
| Encryption | Encrypts traffic in transit to stop outsiders from reading or tampering with data | Encrypts traffic and inspects it for threats or policy violations in real time |
| Routing | Sends all data through a company-controlled VPN gateway | Routes traffic through distributed cloud points of presence for faster, local access |
| Scalability | Limited by the capacity of on-site VPN hardware and gateways | Scales automatically through the cloud without extra equipment |
| Security scope | Protects data during transit but relies on other tools for wider security | Combines encryption with filtering, identity checks, and threat detection |
| Management | Managed through company VPN servers and concentrators | Managed through cloud dashboards with centralized policy updates |
A business VPN creates a secure tunnel between your device and the company network. Once connected, all traffic passes through a company-controlled gateway, where it’s decrypted and sent to internal systems or the internet. This setup of site-to-site or remote-access VPNs works well for smaller networks, but it can be more difficult to scale as organizations grow.
As more people connect, those gateways can become a congestion point. Traffic from different locations often travels long distances to reach a single access point, which can introduce delay and make scaling challenging for globally distributed teams..
SASE changes how those connections work. It sends your traffic to the nearest cloud server instead of routing everything through a single centralized access point. There, it’s verified, encrypted, and filtered.
Security and access controls also check who you are, which device you’re using, and what you’re allowed to reach. At the same time, SASE routes data along the fastest available path to maintain quick connections while inspecting for threats.
SASE vs. MPLS: Speed and cost compared
Multiprotocol label switching (MPLS) has long been the go-to option for linking offices and data centers. It sends data along dedicated, private routes with guaranteed bandwidth, which makes performance fast and predictable. This is one of the main reasons why large organizations have used it for voice, video, and other time-sensitive traffic.
However, MPLS networks are built on fixed infrastructure. Each new branch needs its own circuit, router, and configuration, which often takes weeks, or even months, to set up. Expanding means negotiating with service providers, provisioning new hardware, and managing separate contracts, all of which drive up cost and complexity.
SASE offers far more flexibility thanks to its use of SD-WAN. Network setup and security policies live in one place, too, so you can configure or expand sites remotely without waiting for new circuits.
When traffic increases, the cloud gateways automatically adjust capacity and reroute data through the best available paths. You get reliable, high-quality performance without the long deployment times or high costs of private circuits.
SASE vs. Security Service Edge (SSE): What you need to know
SSE covers the security side of SASE. It brings together ZTNA, CASB, and SWG tools, which are all delivered through the cloud. These services protect people, data, and apps by verifying identity, inspecting traffic, and blocking threats wherever connections start.
The key difference between them is scope. SSE focuses entirely on cloud-based security, while SASE includes both security and network performance. SSE controls who can access what and keeps data safe as it moves between users and cloud apps, but it doesn’t manage how that traffic travels. SASE also adds SD-WAN to handle routing and optimize connections, bringing networking and security together under one framework.
Many organizations start with SSE to strengthen cloud protection, then expand to full SASE when they need unified control over both access and connectivity.
Thinking about switching to SASE?
Moving to a SASE framework can improve both security and performance, but it takes planning to get it right.
Steps to move from old systems
Switching to SASE doesn’t have to happen all at once. It’s best to plan a phased rollout so you can test every layer and make sure everything works correctly. To get started, follow this process:
- Map what you have: List all users, apps, devices, and existing tools to understand how data moves across your network.
- Set goals: Decide what you want from SASE first, such as better visibility, faster access, or stronger security, and define clear success metrics.
- Deploy SD-WAN: Start with a small site or group to improve routing and see how traffic performs before expanding network-wide.
- Integrate identity: Connect your identity provider (such as Azure AD or Okta) to enable secure, role-based access across users and devices.
- Add zero-trust access: Apply authentication and device checks to sensitive apps so only verified users can reach them.
- Move web traffic to the cloud: Use SWG to inspect and filter internet traffic at the nearest SASE point of presence.
- Enable firewall and cloud protection: Apply FWaaS and CASB policies to block risky activity and secure cloud data.
- Migrate in stages: Shift teams and branch offices gradually, monitoring performance and policy compliance after each move.
- Retire legacy systems: Gradually phase out on-site appliances or legacy gateways that are no longer needed once traffic is fully supported by the SASE framework.
- Review and refine: Train staff, monitor logs, and adjust access rules to close any gaps after full rollout.
Will it work with your current setup?
Before you move to SASE, it’s worth assessing how your current network is built and whether it’s ready for integration. First, look closely at what connects your people, apps, and data.
If you already use tools like SD-WAN, cloud firewalls, or an identity provider such as Azure AD or Okta, you may already have part of the foundation in place. SASE builds on these components rather than replacing them completely.
You should also consider how easily your systems share information. SASE relies on visibility across people, devices, and traffic, so you’ll need a clear view of how data moves between on-site networks and the cloud. Check that your existing tools can exchange data through APIs or cloud connectors and that policies can be applied consistently across different environments.
What to watch out for
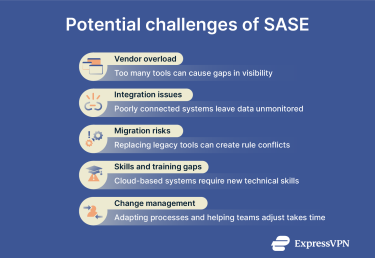 An SASE rollout can streamline how you manage security and networking, but it also introduces new challenges if it’s not planned carefully. The biggest risks can come from using too many vendors or mismatched tools.
An SASE rollout can streamline how you manage security and networking, but it also introduces new challenges if it’s not planned carefully. The biggest risks can come from using too many vendors or mismatched tools.
When different systems don’t integrate smoothly, you can lose visibility into how data moves or where security policies apply. Choosing a single provider, or at least one platform that unifies multiple functions, can help avoid those potential problems.
You should also watch for inconsistencies during migration. As older tools are phased out and new ones take over, there’s a risk of overlapping or conflicting rules. Review your access policies and data routes at each stage to make sure protection stays consistent.
Remember, SASE changes how your team works. Shifting security to the cloud means learning new ways to manage monitoring, logging, and compliance. Invest in training early to help your IT staff adapt to centralized, cloud-based control and make the transition smoother.
Questions to ask before you choose a SASE provider
For SASE to be a success, you need to find a platform that fits the way your network already works, scales with your needs, and keeps management simple.
Should you go with one vendor or more?
SASE can come from a single provider or a mix of vendors that handle different parts of the framework. Using one provider keeps things simple. You get a single dashboard for network and security management, fewer compatibility issues, and faster troubleshooting when something goes wrong. For smaller teams or those just starting with SASE, this approach usually means less complexity.
A multi-vendor setup gives you more flexibility but takes more work to manage. You might prefer one company’s SD-WAN and another’s security stack, but that also means maintaining separate tools, integrations, and support contracts. Make sure the systems use open standards and APIs so they can share policy data and threat intelligence seamlessly.
The right choice depends on your priorities. If you value consistency and simplicity, a single-vendor platform might be the best option. If you already have trusted tools in place and the expertise to integrate them, a multi-vendor model can give you more control.
What features actually matter?
SASE platforms all combine networking and security into one service, but the features they offer can vary. Some key features to look for include:
- Centralized visibility: Real-time dashboards that show how people, apps, and devices connect across your network
- Zero-trust access: Identity-based authentication that verifies every person and device before granting access
- Data protection: Built-in encryption, DLP, and secure web filtering to keep sensitive information safe
- Performance optimization: SD-WAN capabilities and global points of presence that route traffic along the fastest, most reliable path
- Cloud-native network security integration: Compatibility with your existing tools, including identity providers, cloud apps, and security monitoring systems
- Unified policy management: One platform to set, enforce, and update rules across all locations and connection types
How well do they support zero trust?
Zero trust is one of the most important parts of SASE. Without it, anyone who connects to your network could have more access than they should. When comparing providers, look for:
- Continuous verification: A good zero-trust system checks user identity, device health, and context throughout each session, not just at login.
- Granular access control: Access policies should limit people to the apps or data they need, instead of opening the entire network once they connect.
- Device and location awareness: The platform should detect and restrict connections from unknown or high-risk devices and regions.
- Integration with identity tools: Look for seamless compatibility with identity providers like Azure AD, Okta, or Google Workspace to simplify management and ensure consistency.
- Real-time response: The system should automatically adjust or revoke access if a session or device starts to show signs of risk.
Real-life use cases
SASE is flexible and can adapt to different network environments, which also means it’s not a one-size-fits-all solution. It has many different use cases.
SASE for healthcare and finance
If you work in healthcare or finance, keeping data private is critical. SASE helps meet strict compliance rules by enforcing protections in the cloud. Each request goes through multiple checks before it’s approved, including zero-trust authentication, encryption, and DLP.
That means you can access records or financial data securely, even from different sites or remote devices. Every session is verified and logged, helping you protect sensitive information and maintain compliance.
Secure branch connectivity
Retailers, franchises, and other distributed businesses use SASE to connect every location securely through the cloud. Each site gets the same protection and performance without relying on local firewalls or separate VPNs.
When a new branch opens, it connects automatically through the nearest SASE gateway. The system applies security policies and access controls right away, so teams can start working immediately. IT teams manage every site from one dashboard, pushing updates, tracking performance, and fixing issues before they cause downtime.
Mergers and acquisitions
Bringing two companies together often means combining different networks, tools, and security policies, and that takes time. SASE simplifies the process by providing a single, cloud-based framework that both sides can use from day one.
IT teams can add users, devices, and apps under one set of security rules without replacing hardware or waiting for new circuits. Employees can also start collaborating securely from day one, while IT aligns systems and fine-tunes policies in the background.
FAQ: Common questions about SASE
Is Secure Access Service Edge (SASE) better than a VPN?
Not necessarily, as they solve different problems. A business VPN creates a secure tunnel between devices and the company network to keep data private while it travels across the internet. It’s ideal for small teams or fixed sites that need encrypted remote access.
SASE includes that same encryption but extends it through the cloud. It adds cloud-based security checks, identity verification, and network optimization. You still get secure access, but with broader protection and performance. It’s better suited to large or distributed networks where people connect from many different locations and devices.
What’s the difference between SASE and SSE?
Security Service Edge (SSE) focuses only on security. It delivers tools like zero-trust access, data protection, and web filtering from the cloud. Secure Access Service Edge (SASE) includes all of that, but also software-defined wide area network (SD-WAN) for routing and performance, combining security and networking into a single framework.
Can SASE work with my current security tools?
Yes. Most Secure Access Service Edge (SASE) platforms are designed to integrate with what you already use, such as firewalls, VPNs, and identity providers like Azure AD or Okta. If you’re thinking about switching to SASE, it’s worth assessing your current system first to make sure it can work for your setup. You can roll it out gradually, connecting your existing systems before phasing out older tools.
What are the biggest Secure Access Service Edge (SASE) challenges?
One of the biggest challenges of SASE is integration. Combining networking and security in the cloud requires careful planning to avoid gaps or overlapping policies. Some teams also need extra training to manage cloud-based systems effectively and keep visibility across all connections.
Is Secure Access Service Edge (SASE) right for small businesses, too?
Yes, but only if you need it. For smaller networks or single offices, a corporate VPN or standalone security tools might be enough. SASE is most useful when you have multiple locations, remote teams, or a growing cloud infrastructure and need consistent protection everywhere.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN